General Discussion
Related: Editorials & Other Articles, Issue Forums, Alliance Forums, Region ForumsWhat the New NSA Docs Show: How They Lied to Us, and a Lot More
Last edited Mon Jul 1, 2013, 01:01 PM - Edit history (21)
For weeks, uncertainty about how the NSA surveillance system - PRISM - actually operates has fueled fierce debate about whether the Obama Administration has been fully candid in its representation of the Agency’s programs.
Release of a new set of slides appears to have answered many of these uncertainties. We can now say with far greater assurance how the NSA actually works and that the President and senior officials have made inaccurate statements.
These documents reveal a substantial amount of new information about PRISM processes and operations, including: http://www.washingtonpost.com/wp-srv/special/politics/prism-collection-documents/ And related article. http://www.washingtonpost.com/investigations/us-intelligence-mining-data-from-nine-us-internet-companies-in-broad-secret-program/2013/06/06/3a0c0da8-cebf-11e2-8845-d970ccb04497_story.html
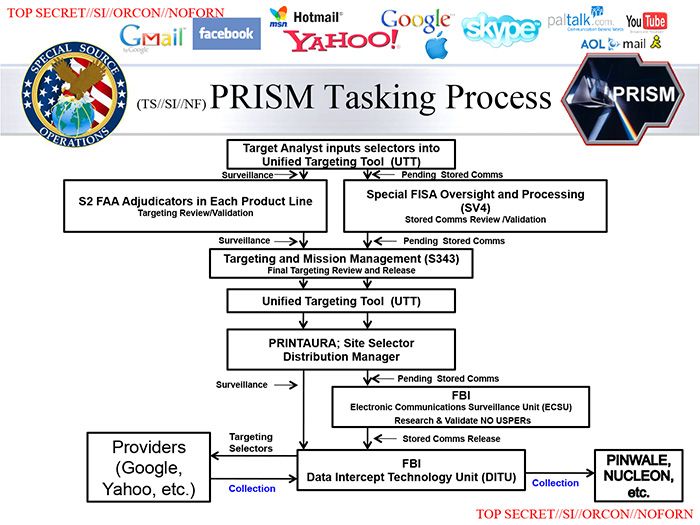
SLIDE 1 – PRISM Tasking Process
• The PRISM database contains both CONTENT and METADATA.
• Content (voice messages) is indicated as PENDING STORED COMMS.
• The TARGETING REVIEW AND RELEASE process involves PROFILING.
• This partially automated PROFILING process employs both real-time SURVEILLANCE data and PENDING STORED COMMS in the decision to target an individual.
• The determination that a potential target is a US PERSON is made by the FBI after profiling has identified the subject.
• Profiling involves searches of databases of other Agencies, including foreign intel service databases
• A warrant is NOT used for this initial PROFILING step.
• The PROVIDERS (Google, Yahoo, etc.) provide additional data after targeting is completed (all targeting data provided stays in the database and informs subsequent profiling decisions.)
• NUCLEON analyses the Voice Content released from the PRISM database.
• PINWALE does the same for email content.
SLIDE 1 (original)
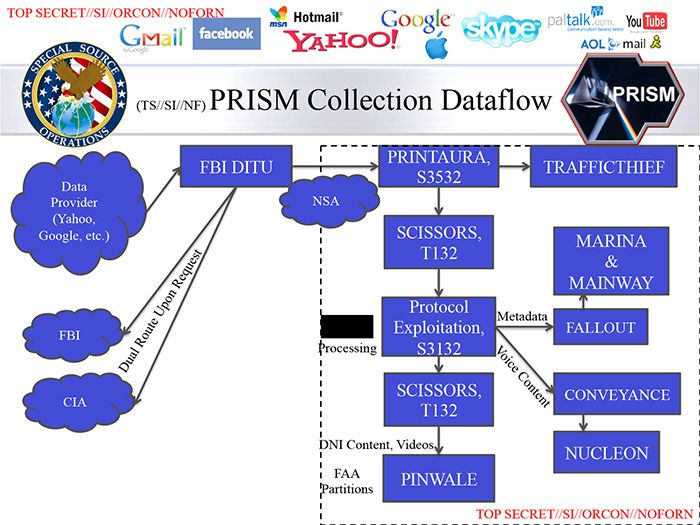
SLIDE 2
The next slide gives us further detail about the use of voice CONTENT in PRISM:
• Voice recognition and Internet are part of PRISM - it isn't just metadata!
• PRINTAURA automates the traffic flow. SCISSORS and Protocol Exploitation sort data types for analysis in NUCLEON (voice), PINWALE (video), MAINWAY (call records – phone metadata) and MARINA (Internet records).
• In addition to NUCLEON, there is a second voice data program named CONVEYANCE, which appears to be a splitter.
• This slide also shows voice CONTENT is being acquired as part of the same program.
• The claim that PRISM does not contain voice content, just metadata, is simply untrue.
• Voice Metadata goes to MARINA and Internet records are analyzed and stored in MAINWAY.
SLIDE 2 (original)
SLIDE 3: There are 10 Types of Content within PRISM
• The PRISM case notation format reflects the availability, confirmed by The Post's reporting, of real-time surveillance as well as stored content.
• SLIDE 3 shows there are 10 types of CONTENT stored within the PRISM database:
B. IM (chat)
C. RTN-EDV (real-time notification of an e-mail event such as a login or sent message)
D. RTN-IM (real-time notification of a chat login or logout event)
E. E-Mail
F. VoIP
G. Full (WebForum)
H. OSN Messaging (photos, wallposts, activity, etc.)
I. OSN Basic Subscriber Info
J. Videos . (dot): indicates multiple types

• NOTE A, SLIDE 3: Voice data appears to be designated “Content Type: STORED COMMS" (Except VoIP)
STORED COMMS is US person voice (and email) content. There is no other other type of content that US person voice content might fit into, and by a process of deduction, nothing else that STORED COMMS might be. Also, please note in Slides 1 and 2, PENDING STORED COMMS is shown to have its own separate process stream inside the PRISM database, and it is not SURVEILLANCE that may be acquired after the warrant is issued. This seems to answer two questions: whether content informs the targeting decision; and, is it gathered before or after a warrant is issued?
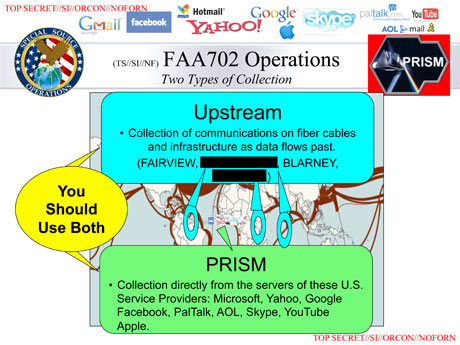
Clearly, as these and earlier documents show, the PRISM system and analysts have access to vast amounts of data at the profiling stage before the targeting decision is made, and as NSA interprets the law, this profiling step does not require a FISA warrant under the 2008 FISA Amendement Act (FAA). In addition to content taken from the 8 Internet Service Providers, the PRISM program also taps into fiber cables "upstream" (at international points of ingress/egress to the US and abroad), as shown in the "FAA 702 Operations" slide, June 8 Guardian slide below: http://www.guardian.co.uk/world/2013/jun/08/nsa-prism-server-collection-facebook-google
Indeed, it is virtually certain that large amounts of US person data are available without warrants to NSA personnel, at least in the files of other agencies that analysts and contractors may access in the process of profiling suspected terrorists and other NSA targets. Under the law as it was changed by the PATRIOT Act, analysts have 72 hours to examine US person content before they have to seek a warrant. See FISA, 50 U.S.C. § 1801(h)(4): http://www.law.cornell.edu/uscode/text/50/1801
Furthermore, NSA and its contractors have a full week to seek a FISA warrant under "exigent circumstances". 50 U.S.C. § 1805(e)(3): http://www.law.cornell.edu/uscode/text/50/1805
PRISM is a “database of databases.” Analysts have access to many databases, both domestic and foreign intelligence agencies, and those contain information from all sources – and they generally are not minimized to segregate US person information. According to the sequence of steps shown in SLIDE 2, US person voice content does get separated out and sent to NUCLEON, and the metadata is deposited in MARINA, but only after a US person has gone through the profiling process. This suggests that US person content is utilized in some way at the initial profiling stage of PRISM, which appears to skirt the intent of FISA, if as we see below, loopholes allow it's use in practice.
Under the law, US person telco content is supposed to be "minimized" under Sec. 215 of the PATRIOT Act, and Sec. 216 is supposed to do the same for US person Internet records. Meanwhile Sec. 702 of the 2008 FAA (FISA Amendent Act) legalized the sort of targeted NSA activities that PRISM carries out, but that targeting is supposed to be restricted to foreign persons abroad. Nonetheless, because of loopholes in the law -- such as the allowance under Sec. 1801(h)(4) and 1805(e)(3) for up to seven days of unfettered viewing of US person data that has been worked into PRISM's Tasking process (profiling) -- it does not look like the FISA wall that is supposed to separate these two NSA programs provides any real separation.
• NOTE B, SLIDE 3: NSA intercepts email, on-line chats in real-time, CONTENT TYPES C,D
This appears to answer some of the issue of whether analysts can access communications in real-time, or whether they have to wait for a warrant. That question was raised by this report in CNET: http://news.cnet.com/8301-13578_3-57589495-38/nsa-spying-flap-extends-to-contents-of-u.s-phone-calls/
Rep. Jerrold Nadler, a New York Democrat, disclosed on Thursday that during a secret briefing to members of Congress, he was told that the contents of a phone call could be accessed "simply based on an analyst deciding that."
If the NSA wants "to listen to the phone," an analyst's decision is sufficient, without any other legal authorization required, Nadler said he learned. "I was rather startled," said Nadler, an attorney and congressman who serves on the House Judiciary committee.
Not only does this disclosure shed more light on how the NSA's formidable eavesdropping apparatus works domestically, it also suggests the Justice Department has secretly interpreted federal surveillance law to permit thousands of low-ranking analysts to eavesdrop on phone calls.
James Owens, a spokesman for Nadler, provided a statement on Sunday morning, a day after this article was published, saying: "I am pleased that the administration has reiterated that, as I have always believed, the NSA cannot listen to the content of Americans' phone calls without a specific warrant." Owens said he couldn't comment on what assurances from the Obama administration Nadler was referring to, and said Nadler was unavailable for an interview. (CNET had contacted Nadler for comment on Friday.)
Because the same legal standards that apply to phone calls also apply to e-mail messages, text messages, and instant messages, being able to listen to phone calls would mean the NSA analysts could also access the contents of Internet communications without going before a court and seeking approval.
Bear in mind two things: the system seems to handle phone, internet, and email messages differently, and under FISA as revised by the PATRIOT ACT, NSA analysts and contractors have 72 hours to do what they want with all data before seeking a warrant. A warrant is only required if the decision is made to target the individual.
PRISM PROFILING estimate: 90 million callers each month.
SLIDE 4 shows that 117,000 persons were profiled as of April 5, 2013. That may not seem like a very large number. But, NSA analysts are also trained to look at all communications, “two hops” out from a targeted person. The implication of that is that the initial PROFILING step outlined in SLIDE 1 profiles very large numbers of persons, and thus has no real 4th Amendment protection for US persons profiled.
How can that be if the system segregates US person data and is court approved? Look at SLIDES 1 and 2, again. Keep in mind the flow chart that shows how PRISM works. Everyone who has been in communication with those 117,000 targets indicated in SLIDE 4 is also investigated, and (at another “hop”) everyone they have been talking to or emailing or texting or chatting on Internet boards. Because these numbers grow exponentially with each hop, that means that if those 117K persons targeted by PRISM called 30 people that month, and they in turn called 30, the PRISM analysts will have initiated investigations of some 90 million persons each month. That could be more than a billion people each year are profiled. Profiling on this vast scale is consistent with known NSA's statistics: http://www.guardian.co.uk/world/2013/jun/27/nsa-online-metadata-collection
"On December 31, 2012, an SSO official wrote that ShellTrumpet had just "processed its One Trillionth metadata record" . . . (five years ago it)"began as a near-real-time metadata analyzer … for a classic collection system", the SSO official noted: "In its five year history, numerous other systems from across the Agency have come to use ShellTrumpet's processing capabilities for performance monitoring" and other tasks, such as "direct email tip alerting."
Almost half of those trillion pieces of internet metadata were processed in 2012, the document detailed: "though it took five years to get to the one trillion mark, almost half of this volume was processed in this calendar year".
SLIDE 4

The PRISM profiling process contains virtually no safeguards, and here is why:
1) The PRISM Tasking Process flowchart describes an NSA profiling process that does not involve the FBI at any level until the very end, when the FBI ESCU determines the suspect is or is not a US person.
2) The first step in the PRISM process is conducted by software that searches a series of interlinked databases and assembles a predictive profile. The scoring on that profile determines the subject as a potential target. Bill Binney describes that profiling process here: http://civic.mit.edu/blog/schock/the-government-is-profiling-you-william-binney-former-nsa
3) Until the FBI determines that the subject is a US person, the subject is presumed to be a non-US person, and the profiling part of the system affords no 4th Amendment protections in the warrantless search of an array of databases, including those of other US and foreign intelligence services.
4) During this tasking (profiling) stage, the analyst also has access to a near real-time take of the subject's internet activities and chat. No warrant is required for the analyst to carry out this human component of the profiling process. That is described at greater length here: http://www.democraticunderground.com/10023134820
5) The analyst has 72 hours to search across NSA and outside agency databases, as well as real-time monitoring, from the time an anticulable suspicion is raised. During that investigation, supervision is minimal, and the analyst does not have to seek additional permission or a warrant. This initial profiling step is probably the unsupervised analyst's activities that Snowden was describing.
• The metadata focus is the shiny object. The issue is profiling, which does not involve probable cause.
The metadata focus is the shiny object. The issue these new slides raise is profiling – they illustrate how the system profiles suspected callers -- and, many, many more who are called, at least "two hops" out.
Profiling works this way: even though the content of phone and email messages is supposed to be segregated within the databank, the system relies upon algorithms that are built upon all sources of information -- including other US and foreign intel agencies -- to identify possible terrorists when a call is made, in real-time. Those other databases (CIA, FBI, MI6, Saudi MID) inform the NSA PRISM database, but they don't reliably separate (or minimize) US person from foreign person information, so the initial profiling step effectively has no 4th Amendment protections built into it at all. There is no warrant requirement for this step. The NSA reads the law so that it is free to hoover up all calls, email, and Internet traffic, regardless of the parties being within the US. The courts have interpreted that US persons have some expectation of privacy in the content of their voice and email, but considerably less in other Internet communications, so online communications are not protected, and NSA analysts can access them freely in "real-time" whenever you log on. Finally, the courts have little or nothing to say about government profiling of US persons (provided that it doesn't discriminate), so that is where the Agency operates most freely.
In other words, when you place a call, or go on-line to send a message, you're potentially profiled with an NSA "database of databases" that makes no distinctions between US and foreign persons until at a later stage, the software or an analyst determines the caller isn't a likely terrorist or a foreign person.
Obama’s Misleading Statement to Charlie Rose: “There is no content in that database”
Both parts – content and metadata - go through a single NSA database, and these slide show that. Do you want to know what Obama actually said?
Much of the President's credibility on this issue rides on the accuracy of his assertions made to Charlie Rose two weeks ago that NSA's "2015 program" keeps only phone call metadata and does not collect voice content. As he put it, the NSA doesn't listen to Americans phone calls because that data isn't kept. "There is no content. " But, is that true? The Post's revelation about NUCLEON certainly contributes to the doubts about that claim. It now appears that Obama was describing only one isolated part of the PRISM database, MARINA, where US person call metadata is stored. Now that we have the larger picture, that was very misleading of Mr. Obama. Very misleading.
The President's interview with Rose is excerpted at length, below: http://www.democraticunderground.com/10023050432
Program 215, (the President) said gets data from the service providers like a Verizon in bulk, and basically call pairs.
"Now, if the NSA through some other sources, maybe through the FBI, maybe through a tip that went to the CIA, maybe through the NYPD. Get a number that where there's a reasonable, articulable suspicion that this might involve foreign terrorist activity related to al-Qaeda and some other international terrorist actors.
Then, what the NSA can do is it can query that database to see did this number pop up? Did they make any other calls? And if they did, those calls will be spit out. A report will be produced. It will be turned over to the FBI. At no point is any content revealed because there's no content," Obama explained.
We now see that the President's statement is, at the least, misleading, if not confused: "There is no content in that database."
What Has and Hasn't Changed Since the 2008 FISA Amendment
The pre-2008 FAA Terrorist Surveillance Program (The Program) swept up everything, content included, and assembled profiles of everybody. That's what Binney and Drake tell us, and they were certainly in a position to know. The EFF suits showed the same thing.
What happens now is that all that data has been harvested and resides in a number of gov't agency databases, and is compared to your metadata whenever you make a call or email. If you score high enough based upon the profile (algorithm), the system red flags you for a warrant. The system takes another look at you in the meantime, before FISC issues the warrant (the law gives NSA 72 hrs. to seek a warrant, and 7 days in "exigent circumstances"
Now, someone needs to explain how, in effect, this sort of warrantless universal profiling is really any different from the warrantless targeted surveillance that was going on before?
leftstreet
(36,108 posts)We know the 17+ Intel agencies have bazillions of taxpayer dollars to spend, but what's the point of all this shit?
DURec
morningfog
(18,115 posts)subjects. I find it hard to believe that is the actual number or the only reason the individuals are chosen.
Maedhros
(10,007 posts)you can pad your numbers a bit.
timdog44
(1,388 posts)are in the surveillance business, they can send about 3-4 of them out and follow these terrorists around 24/7.
90-percent
(6,829 posts)If my math is correct, that's approximately one CIA/NSA/TIA/PRISM/employee/intelligence contractor for every one terrorist.
Every new govt agency we create becomes a self perpetuating monster, don't they?
-90% Jimmy
woo me with science
(32,139 posts)who see our Constitution being dismantled and a predatory global corporate state put in its place.
BobbyBoring
(1,965 posts)Gold star for you!
polly7
(20,582 posts)DirkGently
(12,151 posts)At the very, very least, this volume of information is intended in part of U.S. domestic law enforcement. Recent reports now indicate that foreign *economic spying* is also an application.
We need to hack this system off at the knees. The Patriot Act must go. The revisions to FISA being relied upon need to be thoroughly, publicly vetted and scaled back to something that might reasonably resemble actual national defense.
This is what happens when power is wielded in the dark. The driving force is never about the common good. It's to increase political and economic advantage for those with access to it.
Republicans keep talking about all the things we can't afford anymore, like healthcare and unemployment benefits and the mail.
Money drives this thing. We need to turn off the spigot NOW and worry about rebuilding whatever might actually be needed LATER.
KoKo
(84,711 posts)L0oniX
(31,493 posts)criminals ...not some big ass sovereign country of terrorists.
marions ghost
(19,841 posts)blackspade
(10,056 posts)L0oniX
(31,493 posts)hootinholler
(26,449 posts)winter is coming
(11,785 posts)revealed during the Bush years. Most of them were nowhere near being viable, and most of the "terrorists" who'd taken any movement towards actually doing something had been agitated and aided by an FBI infiltrator. Makes you wonder if we'd be better off simply leaving those people alone.
Enthusiast
(50,983 posts)criticism of the financial services industry, the military industrial complex and criticism of a multitude of other corporations like the oil industry or insurance industry. That way, they can keep tabs on their perceived enemies.
They are looking for whistle blowers of one kind or another, especially those that might criticize the NSA or CIA and affiliated protected corporations.
cantbeserious
(13,039 posts)leveymg
(36,418 posts)WillyT
(72,631 posts)AnotherMcIntosh
(11,064 posts)information was so overwhelming that it could not be processed.
The phrase used (and this may be a paraphrase) was that "You can't get a drink out of a fire-hose."
Except for those profiting from this, it makes no sense to build a multi-trillion Niagara-Falls spy system.
kentuck
(111,099 posts)And if they could somehow get their hands on a death ray that would wipe off the face of the earth anyone that disagreed with them, they would. You knew it was a scorpion when you gave it a ride...
ProSense
(116,464 posts)Both parts – content and metadata - go through a single NSA database, and these slide show that. Do you want to know what Obama actually said?
Much of the President's credibility on this issue rides on the accuracy of his assertions made to Charley Rose two weeks ago that NSA's "2015 program" keeps only phone call metadata and does not collect voice content. As he put it, the NSA doesn't listen to Americans phone calls because that data isn't kept. "There is no content. " But, is that true? The Post's revelation about NUCLEON certainly contributes to the doubts about that claim.
...mentioned two separate programs, and acknowledged that content is collected in one program. PRISM is separate from the metadata collection, and it does not contain content.
From the transcript (http://www.democraticunderground.com/10023039098) of the President's interview:
The fact is that WaPo confirms what has already been reported: that PRISM targets foreigners. From the WaPo link:
New slides published June 29
Acquiring data from a new target
This slide describes what happens when an NSA analyst "tasks" the PRISM system for information about a new surveillance target. The request to add a new target is passed automatically to a supervisor who reviews the "selectors," or search terms. The supervisor must endorse the analyst's "reasonable belief," defined as 51 percent confidence, that the specified target is a foreign national who is overseas at the time of collection.
Obama: PRISM Doesn’t Apply To U.S. Citizens
http://www.democraticunderground.com/10022965452
—By Dana Liebelson
1) Surveillance Has Contributed to Thwarting More Than 50 Terror Plots Since 9/11
<...>
2) The NSA Doesn't Need Court Approval Each Time it Searches Americans' Phone Records
NSA Deputy Director John Inglis said that 22 NSA officials are authorized to approve requests to query an agency database that contains the cellphone metadata of American citizens. (Metadata includes the numbers of incoming and outgoing calls, the date and time the calls took place, and their duration.) Deputy AG Cole also said that all queries of this database must be documented and can be subject to audits. Cole also said that the the NSA does not have to get separate Foreign Intelligence Surveillance Court (FISC) approval for each query; instead, the agency merely has to file a monthly report with the court on how many times the database was queried, and how many of those searches targeted the phone records of Americans.
3) 10 NSA Officials Have Permission to Give Information About US Citizens to the FBI
There are 10 NSA officials—including Inglis and Alexander—involved in determining whether information collected about US citizens can be provided to the FBI. It can only be shared if there's independent evidence that the target has connections to a terrorist organization. Inglis said that if the information is found to be irrelevant, it must be destroyed. If the NSA mistakenly targets an American citizen, it must report this to the Foreign Intelligence Surveillance Court.
4) Other Countries are Less Transparent Than the US, Officials Say
Cole said that the FISA Amendments Act provides more due process than is afforded to citizens of European countries, including Germany, the U.K., and France. Alexander added that "virtually all" countries have laws that compel telecommunications firms to turn over information on suspects.
5) Fewer Than 300 Phone Numbers Were Targeted in 2012
NSA officials say that even though the agency has access to Americans' phone records, it investigated fewer than 300 phone numbers connected to US citizens in 2012. The officials did not provide any detail on the number of email addresses targeted.
http://www.motherjones.com/mojo/2013/06/5-new-revelations-nsa-top-secret-surveillance-programs
http://www.democraticunderground.com/10023041631
leveymg
(36,418 posts)This post is based in the points I made in that back-and-forth. Thank you PNWMOM for helping me to identify the arguments and think through the issues. For any third-parties who might be interested, that discussion is here: http://www.democraticunderground.com/?com=view_post&forum=1014&pid=522748
randome
(34,845 posts)So far as we know, PRISM refers to foreign communications only. If you want the rest of us to believe otherwise, dig up some evidence.
[hr]
[font color="blue"][center]I'm always right. When I'm wrong I admit it.
So then I'm right about being wrong.[/center][/font]
[hr]
leveymg
(36,418 posts)Foreign persons get targeted, true, but only after they are first profiled by NSA and then identified as Foreign Persons by the FBI. See Slide 1.
Everyone gets profiled who gets entered into the system, along with everyone they talk to, and everyone they talk to. That's a billion people a year "two hops removed" if PRISM has 171K targeted persons at any one time.
randome
(34,845 posts)You are assuming the worst. And where does that 'billion people a year' come from?
[hr]
[font color="blue"][center]I'm always right. When I'm wrong I admit it.
So then I'm right about being wrong.[/center][/font]
[hr]
leveymg
(36,418 posts)in US databases, according to Reuters. Potentially, anyone who talks to one of them gets run through PRISM.
171,000 PRISM targeted persons x 30 persons called/mo (first hop) X 30 persons called/mo (second hop) X 12 months = > 1 billion.
But, it's worse than that, because the system as its described looks at metadata for each and every call made to see if it connects with any of those 117K and the 875,000 names who are somehow listed in US government databases as suspected of terrorist ties. http://www.reuters.com/article/2013/05/03/us-usa-security-database-idUSBRE94200720130503
By Mark Hosenball
WASHINGTON | Thu May 2, 2013 8:06pm EDT
(Reuters) - The number of names on a highly classified U.S. central database used to track suspected terrorists has jumped to 875,000 from 540,000 only five years ago, a U.S. official familiar with the matter said.
Among those was suspected Boston Marathon bomber Tamerlan Tsarnaev, whose name was added in 2011. The increase in names is due in part to security agencies using the system more in the wake of the failed 2009 attack on a plane by "underpants bomber" Umar Farouk Abdulmutallab in Detroit.
One has to ask, if the government already knows the identities of the real terrorists, what's the point of operating this profiling system?
marions ghost
(19,841 posts)"Profiling happens before targeting."
Seems like a key point to me.
![]() for this thread
for this thread
leveymg
(36,418 posts)Maybe, because it's the very basis of the internal security system, and like crime and police, people can't imagine living without it?
marions ghost
(19,841 posts)points you toward high-yield targets so it makes sense from a logic viewpoint, as long as you forget about privacy.
Yes I think people are used to thinking there is a justification for this kind of profiling.
It seems that the invasion of privacy and mass profiling of Americans and other populations was never at any time, a concern of the US government. The only concern, from the outset, was to circumvent the constitution.
No conscience. That is the part that's chilling, mind-blowing.
These NSA people who would do this to their fellow Americans (& to other nations) really are ruthless predators. They may fool themselves that they are doing a service for the people of this country. But they know at some level that they are in service to the few. And that is OK with them.
Luminous Animal
(27,310 posts)obviously, he hates the President.
usGovOwesUs3Trillion
(2,022 posts)don't wanna muddy the waters ![]()
Zorra
(27,670 posts)midnight
(26,624 posts)jazzimov
(1,456 posts)Plus, you posted some very interesting info that needs to be emphasized in answering your own question: that how the current procedure is "any different from what was going on before? "
First of all, prior to the 2008 FISA Amendment Bush was listening to any call he wanted without a warrant. That was in addition to your statement "The pre-2008 FAA Terrorist Surveillance Program (The Program) swept up everything, content included, and assembled profiles of everybody."
In your own statements you say "the system red flags you for a warrant." That's the first change. Also, the new system does not allow "everybody" to be targeted. First of all:
The request to add a new target is passed automatically to a supervisor who reviews the "selectors," or search terms. The supervisor must endorse the analyst's "reasonable belief," defined as 51 percent confidence, that the specified target is a foreign national who is overseas at the time of collection.
Then, according to the link:
For stored communications, but not for live surveillance, the FBI consults its own databases to make sure the selectors do not match known Americans.
And further:
The systems identified as FALLOUT and CONVEYANCE appear to be a final layer of filtering to reduce the intake of information about Americans.
Further, although the database may be capable of storing content does not mean that it does. Another difference from the pre-2008 amendment is that before the private companies were forced to turn over all data. After the changes, they were required only to turn over the data requested by a FISA court warrant. If you read the FISA warrant that was leaked to the Guardian that was sent to Verizon, the order specified NO CONTENT.
http://www.guardian.co.uk/world/interactive/2013/jun/06/verizon-telephone-data-court-order
These court orders specify which data is input into the database. Again, yes because it CAN doesn't mean it DOES.
Further, since the 2008 FISA Amendment, the FISA courts require Congressional oversight.
randome
(34,845 posts)[hr]
[font color="blue"][center]I'm always right. When I'm wrong I admit it.
So then I'm right about being wrong.[/center][/font]
[hr]
leveymg
(36,418 posts)In effect because of the way PRISM operates, I am arguing, that is really not as big a difference from STELLAR WIND as it may seem. Warrantless profiling seems just as odious to me as warrantless targeted analysis.
The present system like the old one primarily operates according to social mapping. But, given the large numbers involved when you do just a few hops, and have an existing suspect base of 171,000 (PRISM) to 875,000 (all USG databases), up from around 500,000 a few years ago, the numbers of persons profiled becomes very large.
ProSense
(116,464 posts)"The bottom-line, instead of warrantless targeting, the system now is warrantless profiling everyone. In effect because of the way PRISM operates, I am arguing, that is really not as big a difference from STELLAR WIND as it may seem. Warrantless profiling seems just as odious to me as warrantless targeted analysis. "
Not only are you comparing actual spying to the collection of data, but you're also comparing an illegal spying program that bypassed the FISA court entirely with a court approved program that targets foreigners. The scope is likely a problem, but there are checks in place: http://www.democraticunderground.com/10023060180
stevenleser
(32,886 posts)CakeGrrl
(10,611 posts)And that's the problem. The assumption that technological potential equates to warrantless surveillance.
It's a simple matter of choosing to believe Snowden's unproven assertions over the process...and displaying the information that supports the unproven assertions.
hopemountain
(3,919 posts)or attempts on the lives of the american administration
it is also about the highly complex & corrupt other means of making and laundering money.
technology
drugs
sex
child pornography
human slaves
weapons
black market
etc., etc.
it is far >117,000 - or 3,000 as someone else ventured
it is a tangled mass of darkness.
Galraedia
(5,026 posts)Conspiracy!!! They're coming for the LOLcat photos you e-mailed your family and friends. Run for the hills!
leveymg
(36,418 posts)Just thinking the issues through from a slightly different perspective to draw my own conclusions and raise my own follow-up questions.
If you want to argue with any of that, fine. But, don't be obnoxious with the usual cliche CT meme. It's a worn-out meme and doesn't reflect well on you. Get more creative.
Galraedia
(5,026 posts)CONSPIRACY! The MSM can't be trusted! THEY'RE COMING!!! THE GOVERNMENT IS COMING! Put on your tinfoils hats before they try to infiltrate your brain with their ultrasonic death rays!
leveymg
(36,418 posts)Don't overwork the poor little thing. ![]()
FirstLight
(13,360 posts)this is just abhorrent to me in a constitutional democracy...but we haven't had that for many years now.
I bet many of those who are filtered and targeted are involved with Occupy, et al...
on the one hand it steams me...on the other it scares me...
I have no faith in govt
snot
(10,529 posts)leveymg
(36,418 posts)nineteen50
(1,187 posts)is being used to determine the intent and timing of dissent and protest in order to control and defuse it. It is the new favorite tool of the power-elite oligarchy, which owns both political parties and has wrapped itself in the authority and cloak of the American Government.
Sancho
(9,070 posts)Maybe Obama is finding out about the same time that the public does...just saying.
Douglas Carpenter
(20,226 posts)live in a bubble. There is almost no way to avoid living in a bubble for someone in such a position. They by nature find themselves relying on the security state and probably rarely hear a whole lot of input from sources other than the security apparatus.
90-percent
(6,829 posts)Makes you wonder if it's even possible for Obama to surf the net like us average people.
-90% Jimmy
Politicub
(12,165 posts)I don't think it's only the incessant bashing of the president that's misplaced, it's the gullability that so many on DU have when it comes to anything supporting their paranoia.
Like the OP. It relies on so many assumptions that there is no reasoned debate or discussion to be had. If a discussion point from critics challenges the OP's assumptions, then someone else comes along, shrieks and just makes something up. Usually they end their wild-eyed freak out by saying that they'll never vote democratic again.
If we are honest with ourselves, then we have to admit the verifiable public information out there is slim. But don't let that stop you from making stuff up.
Rational discussion has given way to conjecture. It's no different than an argument with a Christian fundamentalist who covers his poor argument with the fig leaf of his interpretation of god.
leveymg
(36,418 posts)in a position of access and interest -- like the White House or NSA -- would have spoken up by now to tell us they were faked? Geez, speaking of conjecture.
marions ghost
(19,841 posts)that the Wapo was given tell you they are authentic. Besides, the Washington Post is not the New York Post (Rupert rag)--the standards are a lot higher. Barton Gellman of the Wapo gave these source documents credibility.
Try again. Ya got nuthin'
Douglas Carpenter
(20,226 posts)H2O Man
(73,558 posts)Recommended.
leveymg
(36,418 posts)My pleasure.
H2O Man
(73,558 posts)of "old times" on this forum. Definitely the same high-quality that makes DU worthwhile.
BelgianMadCow
(5,379 posts)and indeed, it's the hardcore thinkers of way back when that are shining by example.
Very heartening.
cali
(114,904 posts)DU at its best and most informative.
a heartfelt k&r
bananas
(27,509 posts)blackspade
(10,056 posts)Thanks for the explanation.
Octafish
(55,745 posts)So, We the People are now our own Catch-22.
Thank you, leveymg. Transparency: It's what democracy needs.
Safetykitten
(5,162 posts)Plus they are charts. Anyone could of done those. And if you are not doing anything wrong, what's the big deal?
Oh, and that guy Snowden? I heard that he did not pick up after his dog at his condo complex.