General Discussion
Related: Editorials & Other Articles, Issue Forums, Alliance Forums, Region ForumsGuardian: "XKeyscore: NSA tool collects 'nearly everything a user does on the internet'"
Last edited Wed Jul 31, 2013, 12:31 PM - Edit history (1)
XKeyscore: NSA tool collects 'nearly everything a user does on the internet'
• XKeyscore gives 'widest-reaching' collection of online data
• NSA analysts require no prior authorization for searches
• Sweeps up emails, social media activity and browsing history
• NSA's XKeyscore program – read one of the presentations
Glenn Greenwald
theguardian.com, Wednesday 31 July 2013 08.56 EDT
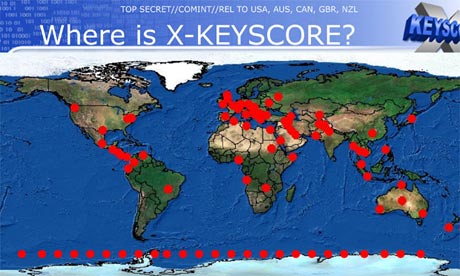
One presentation claims the XKeyscore program covers 'nearly everything a typical user does on the internet.'
A top secret National Security Agency program allows analysts to search with no prior authorization through vast databases containing emails, online chats and the browsing histories of millions of individuals, according to documents provided by whistleblower Edward Snowden.
The NSA boasts in training materials that the program, called XKeyscore, is its "widest reaching" system for developing intelligence from the internet.
...
"I, sitting at my desk," said Snowden, could "wiretap anyone, from you or your accountant, to a federal judge or even the president, if I had a personal email".
US officials vehemently denied this specific claim. Mike Rogers, the Republican chairman of the House intelligence committee, said of Snowden's assertion: "He's lying. It's impossible for him to do what he was saying he could do."
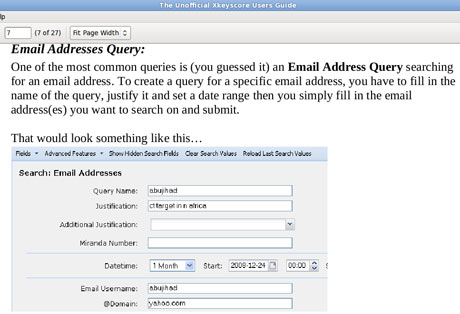
But training materials for XKeyscore detail how analysts can use it and other systems to mine enormous agency databases by filling in a simple on-screen form giving only a broad justification for the search. The request is not reviewed by a court or any NSA personnel before it is processed.
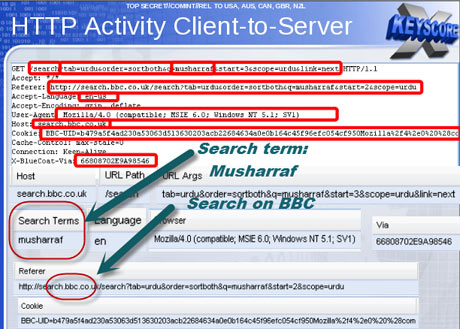
XKeyscore, the documents boast, is the NSA's "widest reaching" system developing intelligence from computer networks – what the agency calls Digital Network Intelligence (DNI). One presentation claims the program covers "nearly everything a typical user does on the internet", including the content of emails, websites visited and searches, as well as their metadata.
Analysts can also use XKeyscore and other NSA systems to obtain ongoing "real-time" interception of an individual's internet activity.
...
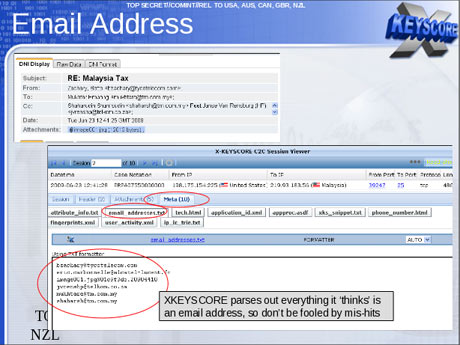
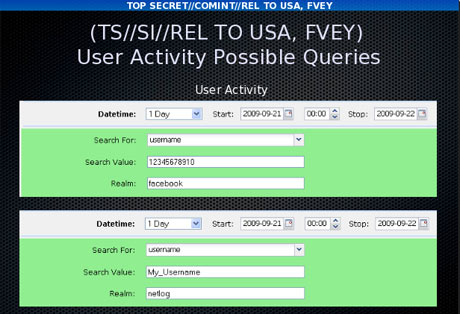
The purpose of XKeyscore is to allow analysts to search the metadata as well as the content of emails and other internet activity, such as browser history, even when there is no known email account (a "selector" in NSA parlance) associated with the individual being targeted.
...
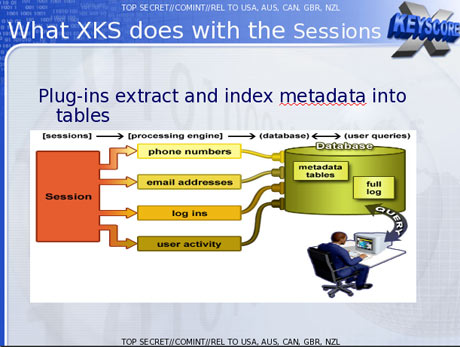
Chats, browsing history and other internet activity

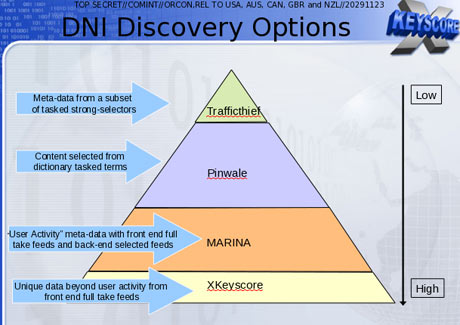
To solve this problem, the NSA has created a multi-tiered system that allows analysts to store "interesting" content in other databases, such as one named Pinwale which can store material for up to five years.
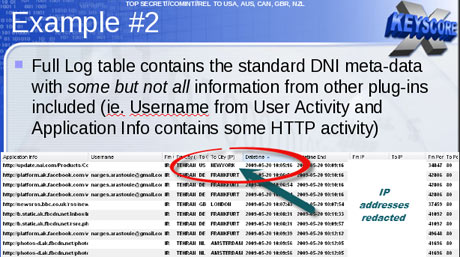
"The government doesn't need to 'target' Americans in order to collect huge volumes of their communications," said Jaffer. "The government inevitably sweeps up the communications of many Americans" when targeting foreign nationals for surveillance.
Acknowledging what he called "a number of compliance problems", Clapper attributed them to "human error" or "highly sophisticated technology issues" rather than "bad faith".
http://www.theguardian.com/world/2013/jul/31/nsa-top-secret-program-online-data
think
(11,641 posts)Perhaps if I click my heels 3 times everything will return to normal....
appal_jack
(3,813 posts)That's 'cuz the NSA never met a datum that they didn't like (& archive...)
I came close to writing "the NSA never met a data that they didn't like," but my sixth grade science teacher's voice in my head shouted me down. It's tough when humor and grammar collide.
![]()
-app
think
(11,641 posts)wouldn't want to be accused of verbal abuse....
![]() for agent Mike
for agent Mike ![]() just in case you don't have a sense of humor
just in case you don't have a sense of humor
reformist2
(9,841 posts)Or is it really Miguel, because the NSA outsourced to Mexico???
The Snoopers have to be "reasonably assured" the any communication they decided to target must be Foreign Traffic.
That has been interpreted to mean that they spies must have at least a 51% chance of your conversation being at least 1/2 foreign before they Record and Compile every fucking you say.
That is [font size=5]a 51% confidence in a target's "foreignness".[/font]
"Flipping a coin, plus 1%"
Here.
John Oliver explains it better that I can:
Good News! You're Not Paranoid
http://www.thedailyshow.com/watch/mon-june-10-2013/good-news--you-re-not-paranoid---nsa-oversight
ConservativeDemocrat
(2,720 posts)Seriously, did you not look at the slides just posted?
I think we've identified the real problem. Greenwald isn't smart enough to understand a simple powerpoint presentation.
- C.D. Proud Member of the Reality Based Community
reusrename
(1,716 posts)The software automatically deals with satisfying all legal requirements established by the FISA courts for both metadata and content.
This is exactly what the software is designed for.
This is exactly what it does.
If there is something that you still cannot understand, feel free to ask questions.
It's like you're barking into the wilderness here. If you need more help with understanding what's going on with this, just ask and maybe someone will be able to get through to you.
usGovOwesUs3Trillion
(2,022 posts)That they can not display due to privacy concerns, which demonstrates more integrity than our government.
think
(11,641 posts)to squelch a conversation....
Catherina
(35,568 posts)You gotta love the newspeak
snooper2
(30,151 posts)Nice to see they are using Linux too-
Yo Greeny, why you redacting pages...I thought you were going to show us EVERYTHING!
bunnies
(15,859 posts)every American who has communications with someone outside of the country would be in this searchable database? Am I reading that correctly?
Catherina
(35,568 posts)Some searches conducted by NSA analysts are periodically reviewed by their supervisors within the NSA. "It's very rare to be questioned on our searches," Snowden told the Guardian in June, "and even when we are, it's usually along the lines of: 'let's bulk up the justification'."
That's how NSA employees were already caught getting their jollies listening to the pillow talk and sex chats of US citizens overseas, to include journalists and military personnel.
That sounds so noble. And the NSA would never abuse its awesome surveillance power, right? Wrong. In 2008, NSA workers told ABC News that they routinely eavesdropped on phone sex between troops serving overseas and their loved ones in America. They listened in on both satellite phone calls and calls from the phone banks in Iraq's Green Zone where soldiers call home. Former Navy Arab linguist, David Murfee Faulk described how a coworker would say, "Hey, check this out… there's good phone sex or there's some pillow talk, pull up this call, it's really funny, go check it out." Faulk explained they would gossip about the best calls during breaks. "It would be some colonel making pillow talk and we would say, 'Wow, this was crazy.'"
http://www.theatlanticwire.com/politics/2013/06/nsa-spying-verizon-analysis/65963/
bunnies
(15,859 posts)fan-fucking-tastic. I feel so much safer now.
think
(11,641 posts)LiberalEsto
(22,845 posts)Oh nooooooooo
![]()
NealK
(1,879 posts)snooper2
(30,151 posts)For example, if mister Asshole terrorist #43 who is British flies to Sudan and gets online. Let's say he is a prime target and he logs into his email and sends one to bunnies@aol.com but the idiot mistyped and meant to send it to bunies@aol.com-
Then your account would be in the database store and when they do a search for information related to the targets account your info would pop up.
For a high level power-point slide if it's all true they have some pretty sharp developers. Being able to programmatically track and categorize indicators based on language is pretty cool.
bunnies
(15,859 posts)Just put in some bogus reason for the lookup and all you need is an email address. If they sweep up ALL communications between Americans and anyone in foreign countries then it wouldnt matter if a suspect contacted me. Im already in that database anyway. ![]()
snooper2
(30,151 posts)bunnies
(15,859 posts)This whole thing hurts my brain. ![]()
snooper2
(30,151 posts)I was told by one vendor that 18% of traffic on the Internet are DDOS attacks, SIP Bots, Malware, etc,.
I'm sure there are some servers where they pull all data...Probably some mail servers and different hosting servers where "bad guys" have web domains.
The problem becomes the number of humans you have to look at data. For example, there are only so many folks who speak Farsi at the NSA. I know first hand the FBI can use some more linguists. They are literally looking for a needle in a haystack. Or I should say, trying to look at 117K needles in a million haystacks when you think of all the web servers, mail servers, and chat communicators in the World.
From these new slides looks like they can basically have "pop-up" notifications when a target say, logs into their email account.
bunnies
(15,859 posts)I guess the "real" problem is its potential for abuse? Id love to see a list of those being targeted. I hope I dont accidentally sell one of them something on ebay. ![]()
backscatter712
(26,355 posts)Most of the traffic can be easily filtered out - DDNS packets can be immediately identified and discarded, for example, as can most kinds of spam.
And the useful bits can often also be easily identified - when you see data going back and forth between a random user and one of Facebook's servers, that indicates it might contain something useful.
But like I said, there's a reason they're building that monster data center in Utah - because they're doing the same thing Google is doing - search engines on a massive scale.
If Google can find useful information in the middle of the Internet and put it at your reach at the click of a mouse, certainly the NSA can do that too.
Except they're not indexing and searching public web pages. They're indexing and searching your metadata, your private emails & phone calls, your social networks...
As for linguistics - again, that can be augmented by software - Google Translate, for example can usually make a comprehensible, if awkward, English translation of any web page in a foreign language. The linguists would only be needed for the tough cases.
I'll say it yet again - the NSA has built Google for Tyrants.
Th1onein
(8,514 posts)Do you REALLY think that this system was actually set up to catch terrorists? Hahaha! They are hoovering all of the data, ALL of it, because they CAN. And, when they want you to tow the line, they've already got your data stored, and then they "collect" it from the database where it's STORED for YEARS, and "target" you by reading it.
Anyone who thinks they're doing this to protect us from terrorists is a complete idiot.
snooper2
(30,151 posts)I like feelings of grandeur as well at times but really, think about it ![]()
Th1onein
(8,514 posts)THINK for a minute. If they get it ALL, they can sort through it at their leisure. You might not be a threat today, or tomorrow, but you might be later on. Things don't always stay the same, especially in times of great change, and this fascist state is marching onward into the future.
Mojorabbit
(16,020 posts)they could be in a whole lot of people's business.
leveymg
(36,418 posts)It appears that the trigger for getting into the database is appallingly remote from reasonable suspicion. Over time, the chances of being misidentified go up with additional analyst and automated searches. Remember, this is a an "intelligent system" that learns from each use or automated search. The Garbage-in problem always applies.
bunnies
(15,859 posts)I thought it was all communications between an American and someone outside of the country. ![]()
hootinholler
(26,449 posts)Using your cell phone gets one in the DB
There is still a question about if telephone content is captured. We know that all internet content is captured (including content of things like skype calls, etc).
leveymg
(36,418 posts)Bushies couldn't resist the temptation. That ability to do targeted wiretapping, as we are told by whistleblowers, was abused from the top down on orders of Dick "The Prince of Dankness".
leveymg
(36,418 posts)the system. The system is partially automated, so that it "reads" all traffic across the network (including CALEA compliant switches and routers, and cable traffic) and if a tagged number or URL or email address is picked up, or a suspicious pattern is detected (e.g., a cluster of persons talking to each other on trak phones, encrypted communications, etc.), it sends an alert. That's the automated profiling step that usually starts a manual search by an analyst. That's one way.
Another way you can get into the NSA database is by the subsequent action of an analyst (NSA employee or contractor) who uses these tools to search up to three hops out for additional evidence. The analyst is supposed to justify a subsequent search step by a targeted party being outside the US. But, the automated profiling step red flags all activity its algorithms have been programmed to treat as suspicious. The analyst's job is to try to confirm the suspicious activity involves a foreign person abroad, and if possible the nature of the threat posed prior to seeking a warrant, which kicks the case to another agency for follow-up investigation.
wow. You certainly know your shit. ![]()
leveymg
(36,418 posts)But, methods, technologies and procedures generally carry over across the Intelligence Community.
I am interpreting this new information on the basis of what I understand about similar, networked government investigative units.
kentuck
(111,110 posts)to ProIntelligence. ![]()
leveymg
(36,418 posts)and pro-Fourth Amendment.
I'll think about it. ![]()
![]()
![]()
questionseverything
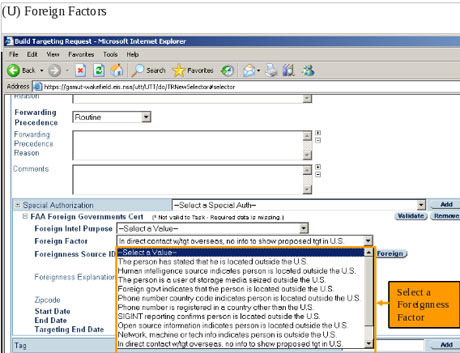
(9,660 posts)One document, a top secret 2010 guide describing the training received by NSA analysts for general surveillance under the Fisa Amendments Act of 2008, explains that analysts can begin surveillance on anyone by clicking a few simple pull-down menus designed to provide both legal and targeting justifications. Once options on the pull-down menus are selected, their target is marked for electronic surveillance and the analyst is able to review the content of their communications:
SO THE "THERE IS NO CONTENT" IS INCORRECT
questionseverything
(9,660 posts)The analyst then selects which of those returned emails they want to read by opening them in NSA reading software.
leveymg
(36,418 posts)That statement by Obama is misleading. It only describes one small compartment of the system analysts can access without a warrant in the process of gathering evidence that might justify seeking a warrant during the 72 hours period -- a loophole in the FISA allows, or as NSA interprets to allow.
Ghost Dog
(16,881 posts)- Edit: & see reply at #202 below
cf. these comments to the Guardian article:
Glenn I sure hope snkwden gave you examples of top officials and how they might be blackmailed. if he did it would nlow this wide open. if he didn't then he will be stuck as a fugitive for a long time.
BTW Glenn given this sory why have you not contacted the whistleblower i think his name is TIce. he has stated that Obama and many others were specifically targeted. Surely what he has to say dovetailes with this and Telling his story here would reach a larger audience.
I have a strong feeling you have no intention of covering what he has to say on a national newspaper like this. Maybe you will stick it in your book
muscleguy 31 July 2013 3:39pm
I assume that the 'damaging information' Snowden has on a dead man's switch for release if anything untoward happens to him includes stuff like this. He says the NSA know what he has got. So it's checkmate to Snowden at the moment despite being besieged.
ZincKidd 01 August 2013 7:24am
I suspect the reason Obama has bent over backwards for the NSA is simply because of what they've got on him. Just like old J. Edgar. Keep your enemies close and your friends closer...
leveymg
(36,418 posts)of unethical and illegal ways. I believe Tice, and it's completely consistent with what I understand Cheney also did at CIA when the Vice President pressured people there to fabricate evidence of Iraq WMD for a cassus belli. Cheney couldn't have done that without the support of top people at both agencies, so it isn't just Cheney.
I think it's interesting that they had their eyes on Petraeus for a long time, under both Bush and Obama, and how rapidly he rose up from a two star to CIA Director, before they finally used surveillance to get rid of him. So, maybe, this watching the watchers thing isn't an entirely bad thing. But, that also assumes that those who are really running the show have enough wisdom to use this power constructively, and I'm not entirely convinced that's always the case.
Th1onein
(8,514 posts)And the crap you are posting sounds suspiciously like the crap that the NSA posted on it's website and then pulled when someone outed it as not being true.
leveymg
(36,418 posts)I wasn't aware that I was carrying water for the NSA, but am curious to hear what you have to say.
Th1onein
(8,514 posts)that is saying that they have to go through a bunch of checks before they can access our data. I don't think that's true at all.
Th1onein
(8,514 posts)YOU ARE ALREADY IN THE DATABASE. EVERYTHING YOU'VE DONE ON THE INTERNET, OR YOUR PHONE FOR THE PAST, AT LEAST, FIVE YEARS. Your data is stored.
When Clapper talked about this, he talked about your data being like a book, on a shelf. When they want to "collect" your data, they simply take the book off of the shelf (ie., pull the data out of the database) and when they "target" you, they read the book (ie., read over your data).
YOU ARE IN THE DATABASE. EVERYTHING.
leveymg
(36,418 posts)It can be as simple as a phone conversation with someone identified as "terrorist" on an NSA list, or as complicated as meeting a profile due to patterns of behavior (using a trak phone or encryption) in combination with other characteristics (ethicity, banking history, education, travels, etc.)
That automated profiling is just the first step in a more intensive profiling process that involves additional systems used by an NSA analyst to identify the person and perhaps something of the nature of the threat.
When I say that someone gets into the system through other databases, I was referring to the 2nd step of the profiling phase, during which the analyst can search across a number of databases.
If this sounds like something the NSA has said, it's because it is based in agency statements and documents leaked and otherwise released. What's wrong with that?
Th1onein
(8,514 posts)Not if you want to target someone to make them tow the line. Say a Congressman, or Senator, that you want vote a certain way. Or a judge, that you want to rule a certain way. Or a juror. Or anybody.
THIS SYSTEM IS NOT FOR FERRETING OUT TERRORISTS. It's used to control us.
leveymg
(36,418 posts)by Dick Cheney. Please, see,
Ghost Dog
(16,881 posts)News organisations and Journalists; US Companies that do international business; Financial Institutions; The State Department; High- and Mid-ranking Military Generals; Law firms and lawyers; The Supreme Court and Judges; High-ranking Intelligence Officers; Barack Obama (and other Senators, Congressmen and candidates)...
Who might be so abusing now, if Cheney was pointed to then?
Tice points to "upper echelons of the intelligence community" as "running the show (the shadow government)."
And they're after Snowden because he got tangible evidence of their misdeeds. And they KNOW he's got MORE.
Th1onein
(8,514 posts)Th1onein
(8,514 posts)You see, they've COLLECTED and STORED everything that you say or do or the internet, and probably on your cell phone, too. Then, only when you are TARGETED do they "take the book off the shelf and read it," as Clapper said.
bunnies
(15,859 posts)whats to stop some random contractor from taking me "off the shelf"? Not that theres a reason to, but they *could* do that, for no reason. Correct?
Th1onein
(8,514 posts)And there are thousands and thousands of contractors, many like Snowden. If Snowden, a high school drop out can get your shit, what's to stop anyone else?
Coyotl
(15,262 posts)and some parts are retained for longer than others.
Th1onein
(8,514 posts)GiaGiovanni
(1,247 posts)?
backscatter712
(26,355 posts)Except it's Twelve Degrees, and Kevin Bacon is Osama Bin Laden... which means everyone's a terrorist, and needs to be tracked!
xchrom
(108,903 posts)leveymg
(36,418 posts)That's a lot of "interesting" data that's being stored without warrants, and it isn't just metadata, and it isn't just foreign persons. Note in Slides 3 and 5, the list of justifications for searching the system for US person data, in addition to a Miranda number (warrant).
Catherina
(35,568 posts)Enjoy
These slides are dated 2008... Their capabilities have increased quite a bit since then
leveymg
(36,418 posts)Major difference. Also, Snowden started as an NSA contractor earlier this year - how did he get five year old training materials, unless they are still in use?
Catherina
(35,568 posts)The date on the full slide set is Feb 2008
http://www.theguardian.com/world/interactive/2013/jul/31/nsa-xkeyscore-program-full-presentation
I'm sure they're still in use, they would have asked that question at the House Hearing I'm sure. How shameful that Obama thwarted that Hearing but all that means is that critics will have even more information and good questions for the September House Hearing.
The Senate Hearing today is just a love fest with the intelligence community. "Thanks for keeping us safe blah blah"
http://www.senate.gov/isvp/?comm=judiciary&type=live&filename=judiciary073113
leveymg
(36,418 posts)If Snowden was given these as part of his NSA orientation earlier this year, these materials indicate that nothing really changed with the provisions of the 2008 FISA Amendment (FAA). The Agency found a bunch of easy workarounds. They certainly buttress his assertions that analysts freely and routinely access the Internet communications of US persons, including content.
It also goes a long way toward confirming what I've been saying for a long time that what NSA is essentially running is a universal profiling system that collects and datamines a wide variety of personal information across databases. The profiling system isn't just about identifying foreign terrorists, but is the successor of Bill Binney's ThinThread system that monitors the population's communications, Americans and foreigners, alike, for characteristics the system has been programmed to associate with "suspicious" activities. That is completely contrary to the 4th Amendment's protection against warrantless searches and seizures.
Sometimes, I hate being right.
Catherina
(35,568 posts)They could come clean with the American people and say "well it used to be that way, but not any longer".
This is why Snowden was so upset and said it was killing him to watch NSA officials AND the Gang of Eight lie to the American people without even blinking. Another thing a lot of people are missing is that it's not just Snowden, when Snowden first communicated with Greenwald, his emails specifically said "we"- "we have something to share", "we have something to show you". There are a lot of decent people who work at the NSA, they get hooked by being able to use skills for something they're passionate about that don't have a lot of value on the outside world, like math skills for code-creaking, language skills and hacking skills. I think they can go on for years, stuck in the fun of those shiny new toys and then one day, for whatever reason, it hits them that what they're doing is wrong. That why the agencies are flipping out and forbidding their employees and students even read the stories. It's not the slides they're worried about but the discussion.
snot
(10,538 posts)Civilization2
(649 posts)nothing illegal happening, no rights being violated,. Greenwald is a libritard, and a bad bad man, who is lying, and has no "evidence",. he just makes this stuff up, because he hates America, and is a racist who don't like that Obama is president, and supports the rethugs,. because they just know it, can feel the truthiness in their guts?
Anyway, hi to those folks, have fun.
truebluegreen
(9,033 posts)Civilization2
(649 posts)that does not lessen its importance!
sabrina 1
(62,325 posts)years' but did nothing to stop it. So Whistle Blowers have to keep blowing the whistle because of the inaction, to put it mildly, of our Government. That is incredible. Some tried, like Ron Wyden but until Snowden's leaks, was basically ignored.
truebluegreen
(9,033 posts)Hippo_Tron
(25,453 posts)I had little doubt that the government had access to all of my online activity if it was interested. But I didn't realize that some junior NSA analyst who I met at a bar one night could go into work the next day and search my activity with little oversight from a supervisor.
Catherina
(35,568 posts)Top Secret//COMINT// REL to USA, AUS, CAN, GBR, NZL
Release to USA, Australia, Canada, Great Britain, New Zealand (the Five Eyes Countries: http://en.wikipedia.org/wiki/Five_Eyes)
http://www.theguardian.com/world/interactive/2013/jul/31/nsa-xkeyscore-program-full-presentation
Civilization2
(649 posts)hootinholler
(26,449 posts)Or some such absurdity.
RC
(25,592 posts)LondonReign2
(5,213 posts)They're working on a dozen new OPs updating us on Snowden's airport adventures and Greenwald's positions from 2003 in the hopes of drowning this out or at least making people waste time countering their distractions.
nadinbrzezinski
(154,021 posts)MisterP
(23,730 posts)that rollback will be
it's not even a matter of delaying us by making us fight them, or demoralizing us: it's about poisoning public discourse by declaring what its limits are--by redefining the very context within which politics is performed, by altering how common sense itself operates ("spies are evil" is rendered more important than "presidential planes are sovereign"![]()
rhett o rick
(55,981 posts)apologists. These revelations are a major shock to their carefully constructed denial bubbles. They believe in blind faith in the Big Daddy and when that "faith" is questioned, they can be nasty.
truebluegreen
(9,033 posts)whttevrr
(2,345 posts)I mean, VOIP doesn't get hoovered, right?
Do people still use 'land lines' anymore?
![]()
Jackpine Radical
(45,274 posts)the nice people who want to help me dump my timeshare, and every politician in the country all call me on my landline.
Th1onein
(8,514 posts)caseymoz
(5,763 posts)That's all I need to know!
![]()
Oh, yeah. K&R
grahamhgreen
(15,741 posts)Harmony Blue
(3,978 posts)Sad and funny in one swoop. ![]()
OnyxCollie
(9,958 posts)And it's stripped of any personal information. We knew about this in 2006; why the outrage?
This is hair-on-fire hyperbole by racists trying to bring down our black President. Plus, Greenwald supported Bush/is a libertarian/lives in Brazil/wrote for the CATO Institute.
So sayeth the Surveillance State Sycophants.
think
(11,641 posts)new memes that will come out?....
![]()
Just having fun of course....
OnyxCollie
(9,958 posts)They're already lazy thinkers.
think
(11,641 posts)and are recycling....
NealK
(1,879 posts)When he was a teen he would pay an adult to buy beer for him.
think
(11,641 posts)keep up the good work citizen spy! I think we've got the goods on him now!
![]()
![]() It shouldn't be necessary but hey thanks for the laughs!
It shouldn't be necessary but hey thanks for the laughs!
NealK
(1,879 posts)nebenaube
(3,496 posts)It is everything.
OnyxCollie
(9,958 posts)Just repeating what ignorant children have said.
grahamhgreen
(15,741 posts)Response to Catherina (Original post)
Marr This message was self-deleted by its author.
gordianot
(15,245 posts)If the NSA can do this it should be safe to assume others also have this capability.
Quantess
(27,630 posts)Remember the massive NSA center being built (in Arizona I believe, IIRC), with billions (or was it trillions) of dollars funneled into running it?
gordianot
(15,245 posts)Missles, tanks, ships are obsolete compared to the new cyber battleground even your own people do not suspect what you can do? It took a major leak to create concern.
xocet
(3,873 posts)
Marr
(20,317 posts)I guess they haven't been told what they think yet.
carolinayellowdog
(3,247 posts)when the "how we feel and how we want to manipulate others' emotions" consensus is reached, by their emoticons shall we know them
Marr
(20,317 posts)Savannahmann
(3,891 posts)About how Greenwald is a real a-hole and doing terrible things and we're dumb enough o fall for the Libertarian/Republican plan to weaken our party.
What a fucking disaster we have become.
leveymg
(36,418 posts)Enthusiast
(50,983 posts)[URL= .html][IMG]
.html][IMG] [/IMG][/URL]
[/IMG][/URL]
leveymg
(36,418 posts)Enthusiast
(50,983 posts)I thought what you said was funny. And I was in agreement. I'm not one of "you guys".
leveymg
(36,418 posts)Seems I'm becoming reflexively defensive after yet another day of battling it out with the deniers on this board. Internet PTSD.
Please accept my apologies. ![]()
![]()
![]()
Enthusiast
(50,983 posts)A natural mistake. ![]()
LondonReign2
(5,213 posts)that they haven't proven anything. It doesn't matter what facts you show them, they say it doesn't prove anything, LOL
Historic NY
(37,453 posts)originally developed for the defense dept. Wow who would have thought. The degrees of separation from its early intended use isn't really that great.
Electric Monk
(13,869 posts)Historic NY
(37,453 posts)TBF
(32,096 posts)besides being a clear violation of the 4th amendment all of this monitoring has got to be freaking expensive! Who is holding the government contracts to do this work and what is it costing the tax payers?
leveymg
(36,418 posts)usGovOwesUs3Trillion
(2,022 posts)Hopefully that will be revealed soon, too ![]()
grasswire
(50,130 posts)Head start for x number of kiddos
Meals on Wheels for x number of seniors
Food stamps for hungry children
Jobs, jobs, jobs
Medical care and benefits for veterans
Infrastructure repairs
....for starters.
It's the biggest heist the world has ever known, I suspect. Bigger even than the war on some drugs, which looted the treasury.
marions ghost
(19,841 posts)TBF
(32,096 posts)Catherina
(35,568 posts)chimpymustgo
(12,774 posts)Coyotl
(15,262 posts)You can well imagine who ended up on a watch list for releasing this secret six years ago.
Deja DU: L. Coyote Nov-09-07
Are ALL COMMUNICATIONS routed overseas to circumvent US law and the Constitution?
http://www.democraticunderground.com/discuss/duboard.php?az=view_all&address=389x2245762
Is that Bush's and the Telecom's HUGE crime hidden and covered-up behind this story?
If the telecoms get immunity, will it aid in covering up Bush's crime.
ABSOLUTELY! That is why it is so important to the Rs! Support = obstruction of justice.
Have we arrived at the point in the history of the Bushco junta where
laws passed and people nominated are part of crimes of obstructing justice?
===================
AT&T Whistleblower: Telecom Immunity Is A Cover-Up
By Spencer Ackerman - Nov 7, 2007
http://www.tpmmuckraker.com/archives/004662.php
Earlier today we flagged that Mark Klein, who uncovered a secret surveillance room run by the NSA ..........
leveymg
(36,418 posts)ECHELON is "Five Eyes," and think that came out in the 1990s along with the insight that "they tap our phones, and we tap theirs."
Catherina
(35,568 posts)People like Mark Klein deserve a medal and a cash award for all the bullshit they were put through.
Coyotl
(15,262 posts)pretty much. The M$M was blissfully unconcerned as they were being spied on.
Even today, everyone forgets the fact that American law only applies in America.
It is NOT illegal to spy on Americans if their communications are routed offshore one inch! This includes a lot more players than the NSA, and more than governments too.
AzDar
(14,023 posts)steve2470
(37,457 posts)Buns_of_Fire
(17,196 posts)Kablooie
(18,641 posts)HardTimes99
(2,049 posts)torture-enabling hacks like Comey to his administration? An easy, albeit ultimately unprovable, explanation is that the NSA and Cheney's goons got the drop on him as of about 2004 (per NSA whistle blower Russell Tice) and put the screws to him on January 20, 2009 and thereafter.
Harmony Blue
(3,978 posts)and only highlights that this issue will not go away.
usGovOwesUs3Trillion
(2,022 posts)This just the kinda information I was looking for in my metadata OP.
Thanks for sharing ![]()
DesMoinesDem
(1,569 posts)Where is the proof? These top secret NSA documents don't prove anything! I don't care that the NSA verified that this program exists. Where is the evidence?! When is Snowden going to come over to my house and give me a demo?
Harmony Blue
(3,978 posts)if you choose to believe this is not real..well...it is your choice. ![]()
DesMoinesDem
(1,569 posts)There is a hint in my title, but it might be hard to tell if you haven't read this person's posts.
Harmony Blue
(3,978 posts)I am the dunce afterall. ![]()
nadinbrzezinski
(154,021 posts)But that was pretty close to what I expect to not see
![]()
sabrina 1
(62,325 posts)Catherina
(35,568 posts)The denials are unbelievable. Not just a river in Egypt lol.
backscatter712
(26,355 posts)IDemo
(16,926 posts)Th1onein
(8,514 posts)backscatter712
(26,355 posts)Th1onein
(8,514 posts)randome
(34,845 posts)Under US law, the NSA is required to obtain an individualized Fisa warrant only if the target of their surveillance is a 'US person', though no such warrant is required for intercepting the communications of Americans with foreign targets.
Are you going to claim I said the technology for this does not exist? I never said that.
Now where is the evidence that the NSA is using this tool to target non-foreign personnel?
So once again, I ask: "Is the NSA using this tool illegally or abusively?" I suspect what your answer is since you seem -for whatever reason- to so willingingly believe anything that dribbles out of Greenwald's mouth.
As usual, Greenwald very carefully lays his verbal trap to lure you in because you so willingly want to keep your hair on fire. He does not point out that there is no evidence if illegality or abuse because he doesn't want you to ask such questions as I posed.
NealK
(1,879 posts)randome
(34,845 posts)Take that, Greenwald!
Civilization2
(649 posts)"since you seem -for whatever reason- to so willingingly believe anything that dribbles out of Greenwald's mouth",.
Track record is important, yours is constant badgering about "proof" and "legality" when we all can see the proofs as they keep rolling out, from all over, not just the individuals you choose to argumentum ad hominem. Everything Hitler did was "legal", according to him. And you know that is not the point! We are debating what is acceptable to us not some corporate-dictators.
randome
(34,845 posts)This is a software tool that the NSA uses. They are required to use it only on foreign individuals. Is there any evidence they are using it for American citizens?
If there is not, then it is not illegal. If you think such software tools should be illegal, I have no problem with that but I think your chances of seeing that happen are nil.
Again, where is the evidence of illegality or abuse? I keep asking this and no one can seem to answer it.
I am not a 'supporter' of the NSA but I do think it's imperative to look at everything critically, including S&G's claims.
Go Vols
(5,902 posts)looks like we will have to wait on another leak.
http://www.democraticunderground.com/10023380596
randome
(34,845 posts)Or misinterpretations. This technology exists and is getting better and faster. It isn't going away. We simply need to learn how to use it safely.
neverforget
(9,437 posts)It's now how we should live.
randome
(34,845 posts)[hr][font color="blue"][center]Don't ever underestimate the long-term effects of a good night's sleep.[/center][/font][hr]
Response to randome (Reply #137)
Go Vols This message was self-deleted by its author.
questionseverything
(9,660 posts)"I, sitting at my desk," said Snowden, could "wiretap anyone, from you or your accountant, to a federal judge or even the president, if I had a personal email".
US officials vehemently denied this specific claim. Mike Rogers, the Republican chairman of the House intelligence committee, said of Snowden's assertion: "He's lying. It's impossible for him to do what he was saying he could do."
But training materials for XKeyscore detail how analysts can use it and other systems to mine enormous agency databases by filling in a simple on-screen form giving only a broad justification for the search. The request is not reviewed by a court or any NSA personnel before it is processed.
///////////////////////
so much for the 3 or 4 supervisors signing off line
randome
(34,845 posts)The technology is to be used for tracking foreign suspects. If there is evidence this is being used for American citizens, let's see the evidence and let the chips fall where they may.
Notice the Guardian article buries that point in the middle of the article.
Enthusiast
(50,983 posts)Claims by defenders of the establishment do not ring true.
The American people recognize there is something fundamentally wrong in the nation. Fundamentally wrong. This wrong is affecting every aspect of the nation. It's right in our face. The government is no longer a 'responsible to the people' representative body.
caduceus111
(132 posts)randome says:
As usual, Greenwald very carefully lays his verbal trap to lure you in because you so willingly want to keep your hair on fire. He does not point out that there is no evidence if illegality or abuse because he doesn't want you to ask such questions as I posed.
Uh, huh. Like these kinds of programs would never be abused. Just like the bulk phone records collection of every single American with a telephone, right?
From today:
Documents show NSA violated court orders on collection of phone records
WASHINGTON — National Security Agency officials violated secret federal court orders authorizing the daily collection of domestic email and telephone data from hundreds of millions of Americans, according to previously top-secret documents made public Wednesday by the Obama administration.
Several senior members of the Senate Intelligence Committee, when approached about the breaches, said they were aware of them but declined to answer questions about their nature.
“I don’t know why you need to ask me,” said the panel’s chairwoman, Sen. Dianne Feinstein, D-Calif.
A spokesman for Sen. Ron Wyden, D-Ore., told McClatchy that Wyden, who is also a member of the Intelligence Committee, was referring to the violations in an interview he gave Tuesday to MSNBC. An outspoken critic of the NSA programs, Wyden said that the breaches involving telephone call data were “serious.”
randome
(34,845 posts)You're going to point to an example of the system working to support your contention that the system does not work.
Might want to see a chiropractor.
Courts rein in LE agencies every day in America. That's how the system works.
Of course any LE agency has the capability of abusing its responsibilities. But I believe we are all in agreement that there needs to be more transparency and less secrecy all around where the NSA is concerned.
Then we can decide if certain practices are abusive and need to stop.
Believing everything that comes out of S&G's mouths is not a good way to evaluate evidence, IMO. Neither of them have shown evidence of illegal or abusive behavior. If the NSA is behaving that way, let's see the evidence and let the chips fall where they may.
[hr][font color="blue"][center]Don't ever underestimate the long-term effects of a good night's sleep.[/center][/font][hr]
fascisthunter
(29,381 posts)and predictable as point and click.
nolabels
(13,133 posts)Catherina
(35,568 posts)
Interesting. From Reporters Without Borders in "Enemies of the Internet, 2013 Report" earlier this year:
BLUE COAT
American Company Blue Coat, specialized in online security, is best known for its Internet censorship equipment.
This equipment also allows for the supervision of journalists, netizens and their sources. (...)
The company also provides network analysis systems called „Intelligence Centres“, which are used by companies and governments to monitor online traffic and identify performance problems. They allow for the monitoring of individual online behaviour.
Blue Coat offers Deep Packet Inspection technology, which can be used to survey and censor the Internet. With DPI, it is possible to look into every single Internet Protocol packet and subject it to special treatment based on content (censored or banned words) or type (email, VoIP or BitTorrent Protocol). DPI not only threatens the principle of Net Neutrality , which Reporters Without Borders defends, but also the privacy of users. It makes single users identifiable and, in countries that flout the rule of law and violate
human rights, often exposes them to arbitrary imprisonment, violence or even torture.
...
DPI is especially threatening to journalists, bloggers, activists and their sources, as it inhibits private, anonymous communication.
leveymg
(36,418 posts)Catherina
(35,568 posts)Catherina
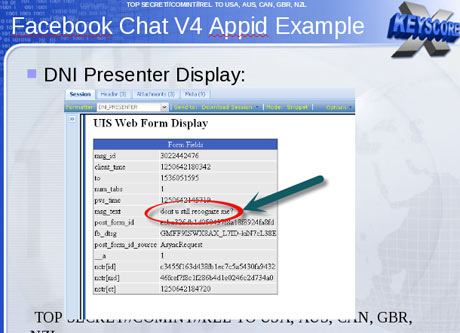
(35,568 posts)
It takes you straight to that person's FB page and personal information.
cantbeserious
(13,039 posts)eom
Xithras
(16,191 posts)"He's lying. It's impossible for him to do what he was saying he could do."
Not "That system doesn't exist."
Not "We can't comment on that."
Not "I've never heard of that program."
Not "Its capabilities don't do what they're claiming."
Not "We only comply with the law."
Not "We're trying to protect you."
Merely "Snowden didn't have access to that." Which really isn't a denial at all.
ljm2002
(10,751 posts)You are right, his statement is carefully worded and your interpretation is right on the money IMO.
Kablooie
(18,641 posts)This technology does seem nearly essential to track down terrorist communications.
I mean we always knew the CIA and FBI had something like this
Bit it certainly is worrying that anyone's Internet use can be grabbed and looked at like this without a warrant.
It seems some kind of warrant system should be required to access.
Allowing this to be used on anyone is extremely dangerous.
The fact that hundreds of people in many companies have access is crazy.
This privatizing of national security is wrong and it's just a matter of time before abuses, that are probably going on right now, become public.
Swede Atlanta
(3,596 posts)The postings are totally void of any meaning but I know they are things our government pays analysts to look at. That way I contribute to keeping them fucking looking for nothing...no payback for our billions or trillions we are paying.
I am glad to burn their resources. It was kind of like the former Soviet Union. It was only when we had burned their resources to the ground that we won. So the more we keep these NSA freaks chasing rabbit holes the better off we are. Eventually when they consume 1/2 of the national GDP the stupid Congresscritters will realize this is stupid and put an end to it.
Harmony Blue
(3,978 posts)And I agree it will reach a point where Congress decides to pull the plug on this shenanigans.
truedelphi
(32,324 posts)the whole reason this Surveillance program is going forward is because our Congress critters are in bed with the Military Industrial Governmental Surveillance Complex. The annual 1.2 trillion dollars of military monies is being diverted over to Surveillance programs.
If you think that the 750 millions of dollars that Richard Blum got for his construction company after we launched the war against the people of Iraq, wait till we find out five years from now how many hundreds of millions of dollars the couple makes on the Surveillance contracts. (Blum is the spouse of Di Feinstein. If anyone here thinks she serves on the Intelligence Committee of the US SEnate for any reason other than padding her and Dickie Poo's fortunes, I don't know what to tell them.)
QC
(26,371 posts)
LondonReign2
(5,213 posts)Last edited Wed Jul 31, 2013, 12:28 PM - Edit history (1)
The NSA could do this in 2008; what are they capable of now?
ProSense
(116,464 posts)Again, Greenwald is talking about "technological capability." He's speculating and has no evidence that any laws are being ignored. The program targets are foreign.
Greenwald is now recycling his breaking revelations.
http://www.democraticunderground.com/10023378966
leveymg
(36,418 posts)The program targets are foreign, but EVERYONE gets profiled as a potential terrorist by the system to determine who will be targeted with a warrant.
Not many of us would argue that sort of universal profiling system was within the ambit of the legislation's framers.
cantbeserious
(13,039 posts)eom
ProSense
(116,464 posts)leveymg
(36,418 posts)got off the ad hominem attacks on Greenwald and Snowden. Your skepticism is welcome, your ax is no longer sharp enough to cut it on this topic. Bury it for a while.
ProSense
(116,464 posts)"You would be more persuasive if you just stuck to the facts about the NSA program and, for a change, got off the ad hominem attacks on Greenwald and Snowden. Your skepticism is welcome, your ax is no longer sharp enough to cut it on this topic. Bury it for a while. "
...I wasn't trying to be "persuasive." I was stating a fact: Making a point isn't a "character assassination."
Those who believe Greenwald should not be criticized are not going to be persuaded, and will continue to use such claims to deflect criticism. I'll, repeat my point, which clearly was not a "character assassination":
Yeah, it's good to know these training documents exists, and the best part:
Again, Greenwald is talking about "technological capability." He's speculating and has no evidence that any laws are being ignored. The program targets are foreign.
Greenwald is now recycling his breaking revelations.
http://www.democraticunderground.com/10023378966
leveymg
(36,418 posts)You post so much, are you partially automated? Also, you never addressed my point about the system being inconsistent with Congressional intent. Please engage on that.
randome
(34,845 posts)I believe Congress fully intended for the NSA to monitor foreign suspects. In fact, that's the entire reason for the NSA's existence.
ProSense
(116,464 posts)"You post so much, are you partially automated?"
Post counting is now being used to deflect. Let me share some facts:
- I am not the DUer with the most posts.
- There are posters who start nearly twice as many threads as I do on any given day.
- I tend to participate in my threads, mostly responding to attempted deflections and personal attacks.
leveymg
(36,418 posts)But, I'd rather keep the dialogue on point and not make this a personal pissing contest. You never answered my question about whether you think this system conforms with the intent of Congress.
xocet
(3,873 posts)LondonReign2
(5,213 posts)it's the "this proves nothing, this is legal" brigade. Alexander could sit in their living rooms running the damn thing and it wouldn't sway them one iota.
Agony
(2,605 posts)Good job!
damnedifIknow
(3,183 posts)and it's in a different country? I've ordered stuff from China before so am I red flagged?
leveymg
(36,418 posts)something the system will retain and if combined with other things, might trip an alarm getting you closer scrutiny.
It's all determined by a very complex set of mathematical algorithms and what else is in there about you.
pecwae
(8,021 posts)use that info for anything other than honorable purposes!
I love that last sentence with the Clapper attributes. My god, do people actually believe these lame excuses?
K&R, Catherina, and thank you for posts on this continuing bullshit.
kentuck
(111,110 posts)To read more closely.
AnotherMcIntosh
(11,064 posts)leveymg
(36,418 posts)PowerToThePeople
(9,610 posts)reformist2
(9,841 posts)Safetykitten
(5,162 posts)sofa king
(10,857 posts)We should all direct our outrage at this President, and be careful to forget about:
The Total Information Awareness Program:
2002: http://www.democraticunderground.com/articles/02/11/21_4th.html
2005: http://www.democraticunderground.com/discuss/duboard.php?az=view_all&address=104x5681899
2006: http://www.democraticunderground.com/discuss/duboard.php?az=view_all&address=364x498378
CARNIVORE:
2004: http://www.democraticunderground.com/discuss/duboard.php?az=show_mesg&forum=102&topic_id=419239&mesg_id=419338
2005:http://www.democraticunderground.com/discuss/duboard.php?az=view_all&address=102x1151853
Domestic surveillance:
2007: http://www.democraticunderground.com/discuss/duboard.php?az=view_all&address=389x2488557
2001--February, 2001: http://www.democraticunderground.com/discuss/duboard.php?az=view_all&address=103x326639
______________________________________
First of all, fuck all of you who have made a ten-year career out of marginalizing the people who reported and passed on these stories, keeping it firmly in the paranoid conspiracy-theory box long enough for the practice to become institutionalized, codified, and legal.
Second, any of you who wish to separate the absolutely criminal practices that created this monster from the civil rights you no longer have today is whistling Dixie. You cannot replace the rights that have been taken from you without also prosecuting the Bush Administration for creating and running this system, illegally, for at least seven years. Bush ain't gonna be prosecuted, so I don't give a flying fuck if you want your rights back now--you simply are not going to get them back because we already allowed it to happen. Ask Ben Franklin about rights not exercised, and what happens to them.
So, third, you can go ahead and try to take apart the American surveillance state now, but it won't work. Instead, your head-on efforts are going to put you and me first against the wall when Jeb steals it.
Our only hope now is to gain control of this apparatus and use it against the people who created it. Destroy Jeb Bush's career before he can get in. Force Dick Cheney to renounce his citizenship and move to Dubai. Wreck Karl Rove with his own disgusting resume. Find the trillion dollars Rumsfeld and Wolfowitz stole. Savage and destroy the careers of top Republican donors.
And, since that ain't gonna happen, either, we have little recourse but to keep pretending we live in a republic until the day when the biological truth forces Americans to eat their oppressors.
LondonReign2
(5,213 posts)You forgot a key date, however:
January, 2009: Obama inaugurated.
Yes, we should have prosecuted BushCo; who is responsible for the failure to do so?
Yes, we should have been rolling back the surveillance capabilities once a Democrat was in charge; who is responsible for the failure to do so?
arely staircase
(12,482 posts)This is the biggest bunch of nothing ever. They have to get a warrant to do it to an individual American other wise it is limited to overseas signals - which is what the NSA does.
randome
(34,845 posts)Why do you hate the truth so much?
arely staircase
(12,482 posts)LondonReign2
(5,213 posts)Nothing else will convince you
marions ghost
(19,841 posts)
(actual logo--Wiki) That eye on the dollar bill is now the eye of global surveillance.
LondonReign2
(5,213 posts)marions ghost
(19,841 posts)when they tried to modify it in 2002--it just grew new arms and names and branched out into different places.
The special domain of a few...
Vashta Nerada
(3,922 posts)Why does the NSA have so much power and authority?
Silent3
(15,270 posts)Not that it justifies spying on HTTP traffic just because it's possible to do so, but anything that people want to keep private should go over HTTPS anyway, or other secure protocols.
Notice, for instance, that Facebook currently works over HTTPS. Banking and credit card sites work over HTTPS. Of course, using HTTPS doesn't guarantee that the government doesn't have an arrangement to collect data directly from the opposite end of such secure connections, but it does prevent snooping of in-transit traffic.
I'm not terribly worried at any rate. I think a lot of the supposed capability of these systems is marketing hype from the people who've created the systems, people who want to get lucrative government contracts.
Xithras
(16,191 posts)If the government intercepts your HTTPS traffic, they merely need to serve a warrant to the cert provider to obtain the keys for the SSL cert used by the site you connected to. Once they have the key, they can decode anything you sent. Facebook uses Verisign certificates. If the government wants to know what you're doing on Facebook, they don't need to get the data from Facebook, they can simply get the cert from Verisign and decode it themselves. In fact, I'd be pretty shocked if the NSA didn't already have the certs from most of the major sites like Facebook and Google on file just for that purpose.
It DOES prevent realtime snooping (because even with the key, the NSA doesn't have the computing power to decrypt every SSL connection in America in realtime), but SSL doesn't do much to protect your data if the government actually has some interest in your data for some reason (and conveniently, the "useless" metadata, which isn't protected by SSL, tells them exactly which certificates they need to use to decrypt everything).
Silent3
(15,270 posts)And if so, not all of them are US companies, so the need for them (or their US offices) to comply, or keep such requests secret, isn't clear to me. Since giving away private keys is giving away a lot, I'd hope that a company issued such a warrant (and especially merely a non-warrant request) would fight it hard, as the scope of what a company gives away when surrendering its own, or a client company's, private keys is huge, much bigger than the scope of any particular suspected communications.
That would be like demanding an entire city allow every home in that city to be searched just because a few homes in the city are suspected of harboring stolen property.
Have things at the NSA (or any other US intelligence operations) gotten that far out of hand? Perhaps, but I'm not quite ready to set my hair on fire yet, as if somehow assuming the absolute worst based on a few accusations and PowerPoint slides is somehow the smart thing to do, so that "they" don't pull the wool over your eyes.
treestar
(82,383 posts)They who have lost all credibility on these things call it an "NSA program" as if someone there invented it. But is is really a program that any company could buy? And then it can be used by the NSA the same way they could use a wiretap.
Boils down to new technology. If private companies have it, the government can get hands on it, too.
usGovOwesUs3Trillion
(2,022 posts)to another computer... once it arrives it is automatically decrypted.
You may not be worried, but you know what they say, ignorance is bliss, but deliberate ignorance is probably bad for your mental health.
Silent3
(15,270 posts)...with I think the point being that such technology can gather a lot of info specifically without having to tap in at the arrival point.
If you want to assume that the government can also tap in at every arrival point, that is I suppose possible, but then the OP story is superfluous to that assumption.
I'm concerned enough with what's fairly certain about the NSA, and what certainly needs reforming, without having to see my hair on fire that every thing I hear MUST BE the "tip of the iceberg", as if the only possible somehow smart thing to do is to assume with great unshakable confidence that "they" can do anything, and can get anything, they want.
usGovOwesUs3Trillion
(2,022 posts)They have TOP SECRET documents, and first hand accounts, indicating they have DIRECT SERVER ACCESS.
Burry your head in the sand if you like, but don't be rude and condescend to folks who are paying close attention, and/or have subject matter expertise in digital communications.
Thanks ![]()
Silent3
(15,270 posts)Yes, there are indications of direct server access, in some places, getting some data. But that's not what this particular XKeyscore story is about. The opposite of having one's head in the sand is not blurring the details of separate stories into one big OMGBBQ.
usGovOwesUs3Trillion
(2,022 posts)In case you don't realize it, these stories are all about 1 thing, NSA Spying by their unprecedented global (yes America included) harvesting, storing, and analyzing of almost ALL of our digital communications.
FYI
Silent3
(15,270 posts)...have been giving, or forced to give, the NSA everything that goes through them and their servers. The extent of any of that is just conjecture. (Somehow the "wise" thing is to assume everything you hear is just the "tip of the iceberg", a defensive stance so automatic for some people they don't even realize when they're doing it it anymore.)
And if it were true that such access was so pervasive, that would make what's being said in the OP about XKeyscore less relevant.
Just because you can pick an umbrella topic ("these stories are all about 1 thing, NSA Spying"![]() doesn't mean that blurring details about separate stories and alleged spying programs under that umbrella topic is warranted or helpful.
doesn't mean that blurring details about separate stories and alleged spying programs under that umbrella topic is warranted or helpful.
usGovOwesUs3Trillion
(2,022 posts)This second release shows the UI of the app they use to pull up the data.
Silent3
(15,270 posts)..."These are the logos of companies we've completed infiltrated/gained complete cooperation from so that we capture and record all of their data"?
usGovOwesUs3Trillion
(2,022 posts)Silent3
(15,270 posts)...and that assures you that it's been proven that the NSA records all data from all the servers from all of those companies? That's the only realistically possible interpretation?
usGovOwesUs3Trillion
(2,022 posts)And their primary mission (spying) paint a pretty clear picture for most reasonable observers.
This law breaking needs to be stopped ASAP!
Join the fight, and pass the word to all your fellows ![]()
bobduca
(1,763 posts)https packets are like sealed envelopes, but they still have internet addresses. which are owned by isps. While you are correct https content is not immediately decryptable its trivial to crack them with a huge data center.
This is why every encrypted packet is saved FOREVER, because terrorists!
Zorra
(27,670 posts)I know for a fact that they have an extensive file on me.
I have been involved in non-violent democratic anti-fascist movements since Vietnam.
What can I do? I have no say in the matter whatsoever.
If I get my way, someday I will have some say in the matter.
Great post. ![]()
snappyturtle
(14,656 posts)Rex
(65,616 posts)use inprivate surfing...DOESN'T MATTER. This is akin to something I always tell people, "if a thief wants to break into your house, he will no matter what you do to protect your property'. IOW, there is NO privacy on the WWW. NOT in one country, NOT in one city. NOWHERE.
And it has been this way since the invention of the BBS. That is over 40 YEARS! If people are getting upset NOW, good! BUT, it has been going on for about 40 years now! Hell, they were wiretapping phones long before anyone even heard of the term! And where does MOST of our technology come from? The military. SAME with the WWW.
IOW, we've all been playing around and surfing on military web servers for decades now.
Amonester
(11,541 posts)Even older with the phones.
Anyone who thought they were using all these gimmicks in total privacy is naïve beyond redemption.
Luminous Animal
(27,310 posts)madrchsod
(58,162 posts)have a nice day spybot!
Liberal_in_LA
(44,397 posts)WillyT
(72,631 posts)sorry i missed this earlier
![]()
![]()
![]()
Catherina
(35,568 posts)I miss so much because DU is moving so fast right now! ![]()
Liberal_in_LA
(44,397 posts)Catherina
(35,568 posts)This only works for unclassified names

Edit: I think it's a safe bet to agree with Greenwald's statement that there's lots more coming lol.

DeSwiss
(27,137 posts)K&R

felix_numinous
(5,198 posts)Catherina
(35,568 posts)New Report Confirms NSA's Ability to Access Americans' Online Activity
July 31, 2013
FOR IMMEDIATE RELEASE
CONTACT: 212-549-2666, media@aclu.org
NEW YORK – The government can easily see the content of Americans' Internet communication and web browsing activities, according to a report published today in The Guardian.
"The latest revelations make clear that the government's surveillance activities are far more extensive and intrusive than previously understood, and they underscore that the surveillance laws are in desperate need of reform," said American Civil Liberties Union Deputy Legal Director Jameel Jaffer, who testified before the Senate Judiciary Committee today about NSA surveillance. "These documents also call into question the truth of some of the representations that intelligence officials have made to the public and Congress over the last two months. Intelligence officials have said repeatedly that NSA analysts do not have the ability to sift indiscriminately through Americans' sensitive information, but this new report suggests they do."
The revelations today come at a time when public opinion has begun to shift in favor of strengthening Americans' privacy rights and a growing bipartisan group in Congress works to rein in NSA surveillance of Americans' communications.
"The seemingly never-ending NSA disclosures show the frightening power the government has afforded itself without the knowledge of the American people," said Michelle Richardson, legislative counsel at the ACLU's Washington Legislative Office. "The recent Amash amendment vote shows that the public has had enough with the blanket, warrantless surveillance of its communications. Without significant reforms to these programs, the government is going to lose them."
http://www.aclu.org/national-security/new-report-confirms-nsas-ability-access-americans-online-activity
randome
(34,845 posts)Does this mean the NSA is violating its own laws and regulations which mandate they can only monitor foreign communications?
Nothing in either of these articles points to that. It's only the ever-fearful 'ability'. They could be spying on all of us. Duh.
[hr][font color="blue"][center]Don't ever underestimate the long-term effects of a good night's sleep.[/center][/font][hr]
Luminous Animal
(27,310 posts)Waiting For Everyman
(9,385 posts)A big "thank you!" to you, and to the other DUers who are keeping us on top of the developments in this situation. Much appreciated!
The only thing that makes me feel a little better about this, is that a lot of people recognize the gravity of it and are duly alarmed about it, including the more thinking people, and thankfully at least some in Congress.
Harmony Blue
(3,978 posts)and more facts are being revealed. Stay informed and we can slowly turn the tide on this massive overreach.
GoneFishin
(5,217 posts)grahamhgreen
(15,741 posts)Fire Walk With Me
(38,893 posts)WASHINGTON (Reuters) - New revelations from former security contractor Edward Snowden that U.S. intelligence agencies have access to a vast online tracking tool came to light on Wednesday, as lawmakers put the secret surveillance programs under greater scrutiny.
The Guardian, citing documents from Snowden, published National Security Agency training materials for the XKeyscore program, which the British newspaper described as the NSA's widest-reaching system that covers "nearly everything a typical user does on the Internet."
Intelligence analysts can conduct surveillance through XKeyscore by filling in an on-screen form giving only a "broad justification" for the search and no review by a court or NSA staff, the newspaper said.
http://news.yahoo.com/u-declassify-documents-spy-programs-surveillance-court-033021541.html
jazzimov
(1,456 posts)which was BEFORE the FISA Act was passed on 07/10/2008. That's when we KNEW that Bush was illegally collecting data and phone calls without a warrant. Which is WHY Congress passed the act in July.
Do they have anything after the Act was passed?
more baloney from the royal funny farm ![]()
blkmusclmachine
(16,149 posts)Response to Catherina (Original post)
Name removed Message auto-removed
Coyotl
(15,262 posts)this thread does not need reposting!
steve2470
(37,457 posts)blackspade
(10,056 posts)I'm glad people beyond progressives are waking up to the facts about these illegal activities.